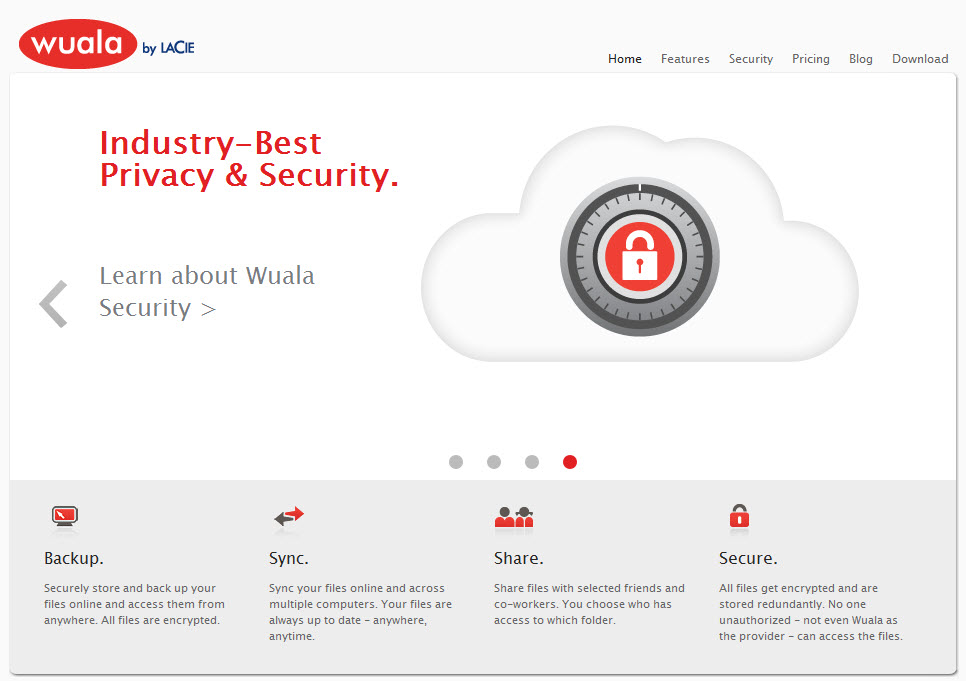
Tag: encryption
I’ll admit that I’m being a bit facetious with the title of this post but there’s a tiny bit of truth hiding in it. This…
Over the weekend I updated from Ubuntu 13.10 to 14.04 LTS and so far I’ve not noticed any significant differences. However, one of my Ubuntu…
The National Security Agency is winning its long-running secret war on encryption, using supercomputers, technical trickery, court orders and behind-the-scenes persuasion to undermine the major…
Pirate Bay founder Peter Sunde is working on a new messaging platform that will be impossible to spy on, even by the people who operate…
The PortableApps.com Carbide encrypted USB drive is the world’s most secure, easy to use flash drive. It uses PIN code access with military grade AES…
BitTorrent Inc. has opened up its Sync app to the public today. The new application is free of charge and allows people to securely sync…
Jeff Atwood over at Coding Horror has posted about something called Rainbow Tables. Now, I don’t want to turn this blog into a discussion of…