 I’ve been putting off this post for a few days to allow for the immediate freak-out to die down and to let some actually good advice to surface. I’m now read to provide the following advice and resources:
I’ve been putting off this post for a few days to allow for the immediate freak-out to die down and to let some actually good advice to surface. I’m now read to provide the following advice and resources:
What happened?
Basically, for the past two years there’s been a flaw in the security software behind somewhere near 60% of all “secure” Web sites on the Internet. That whole “make sure the site you’re logging into says ‘https://'” advice, well, that was the part that was broken. No one stole your password per se, but this hole could allow someone to get it and the site they got it from would have absolutely no idea that it happened.
For a slightly more technical explanation watch this short video from the Security Now podcast.
Is it serious?
Bruce Schneier, the security guy security guys listen to says “‘Catastrophic’ is the right word. On the scale of 1 to 10, this is an 11.” ‘Nuff said.
Do I need to change my passwords?
Yes. Especially if, and I’m sorry if this language offends you, your passwords are crap. And chances are, your passwords are crap. Test your passwords using https://howsecureismypassword.net/. If your password strength isn’t measured in millenia, your password is crap.
Oh, and if you use the same password for more than one site. You password is crap.
This is not news folks. You’ve heard this before and ignorance is no longer bliss when it comes to this stuff.
Do I need to change them right now?
This is the biggest problem caused by this whole mess: it depends.
Services that ran certain types of servers, or non-problematic versions of the SSL software, were not effected by this problem and therefore don’t have this as a reason to need you to change your password. (Unless you should anyway since your passwords are crap. See above.)
Services that were effected need to fix the problem on their end before changing your password will do any good. Sure, you could go change your password right now, but if they fix the problem tomorrow, you’ll just need to change your password again.
(See Naked Security’s “Heartbleed heartache” – should you REALLY change all your passwords right away? if you’d like further details.)
So, how do you tell?
Well, yesterday I got an e-mail from IFTTT.com telling me that they’d fixed the problem and that I should change my password. Full marks to IFTTT but don’t expect that from everyone.
 Mashable has a great page titled The Passwords You Need to Change Right Now where you can look up major services to see if it’s time to change your password. Go there as soon as you’re done reading this unless you’re a LastPass user.
Mashable has a great page titled The Passwords You Need to Change Right Now where you can look up major services to see if it’s time to change your password. Go there as soon as you’re done reading this unless you’re a LastPass user.
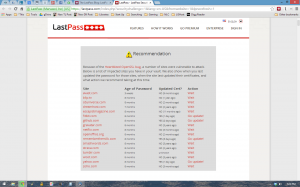
If you use LastPass they have a service that will go through your accounts and let you know which services have the problem, whether they’ve fixed their server or not, and if it’s time to change your password. You can find instructions on how to do this on their page titled “LastPass Now Checks If Your Sites Are Affected by Heartbleed.”
What should I do from this point forward?
Improve your passwords! Seriously folks, we’re not kidding any more. Install LastPass and create a 100% unique and random password for every site you use. Also, if a service uses two-factor authentication and you can do it (i.e. you can receive text messages on any sort of cell phone) turn it on.
If you run a server, or know someone who does, read/send this EFF blog post on Why the Web Needs Perfect Forward Secrecy More Than Ever and do it.
Yes, this is a pain. Yes, things like complex passwords and two-factor authentication, adds some time it’ll take to log into a Web site. But so does locking your door when you leave the house in the morning. That doesn’t mean you’ve wasted the extra five seconds it took just to be a little more secure.