Stay ahead of external and internal threats — and balance performance, reliability, and security with Windows 11. Dave Weston, Windows security expert, joins Jeremy Chapman…
Tag: security
Lorrie Faith Cranor studied thousands of real passwords to figure out the surprising, very common mistakes that users — and secured sites — make to…
Phil Zimmermann, the creator of PGP and Silent Phone is our guest at Google, talking about communications security. How large scale deployments of end-to-end secure…
Thanks to everyone you attended my presentation last night. You were a wonderful group and had great questions. Secure Online Shopping from Michael Sauers
THE TSA IS learning a basic lesson of physical security in the age of 3-D printing: If you have sensitive keys—say, a set of master…
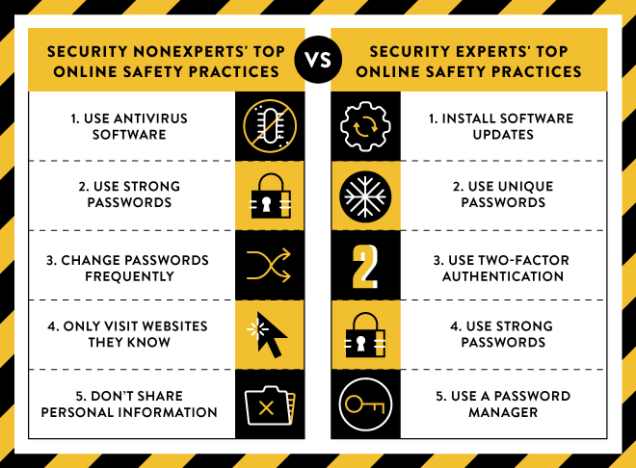
If you ask the average person what the best ways to protect themselves online are, they’ll give some true answers—but they’ll likely be different than…
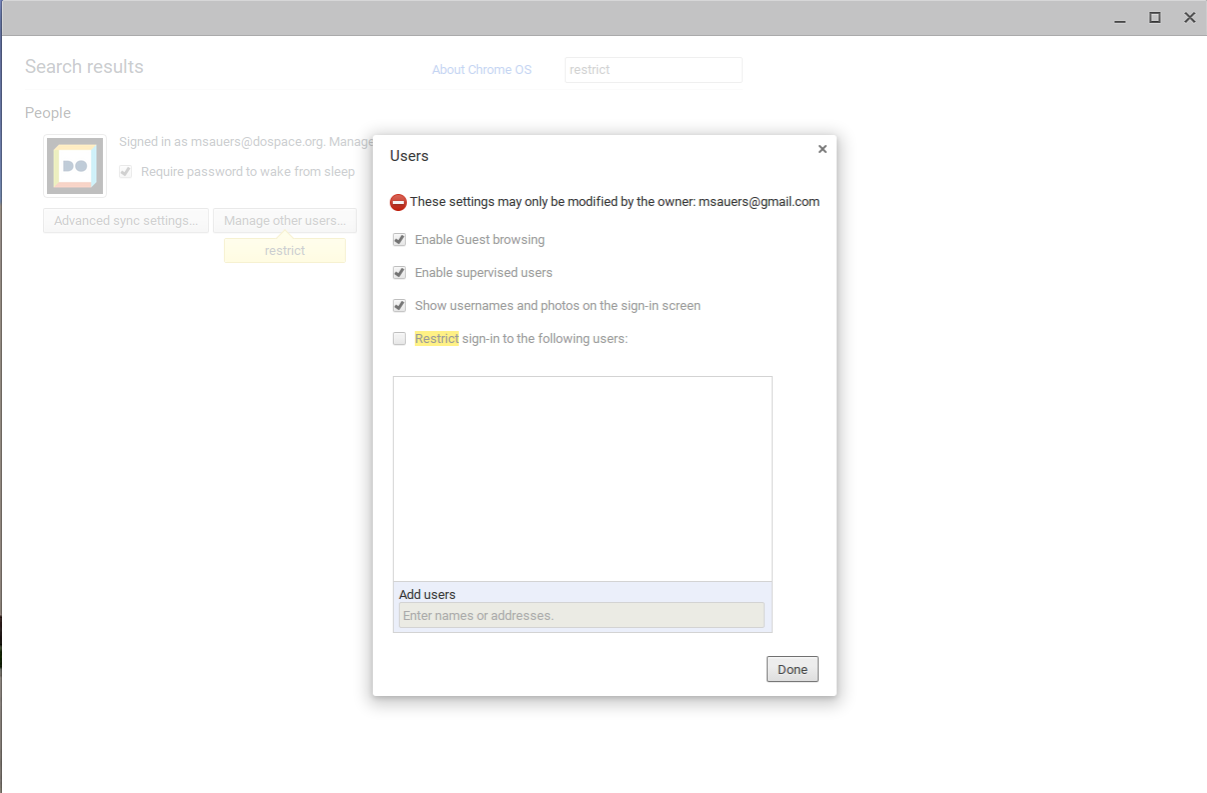
By default the Chrombook allows anyone with a Google account to sign in. But for some, that amount of sharing might be a little too…
There are very few government checks on what America’s sweeping surveillance programs are capable of doing. John Oliver sits down with Edward Snowden to discuss…
Ian Urbina, author of The Secret Lives of Passwords, talks about what passwords mean to people beyond their access to email or social networking accounts.…